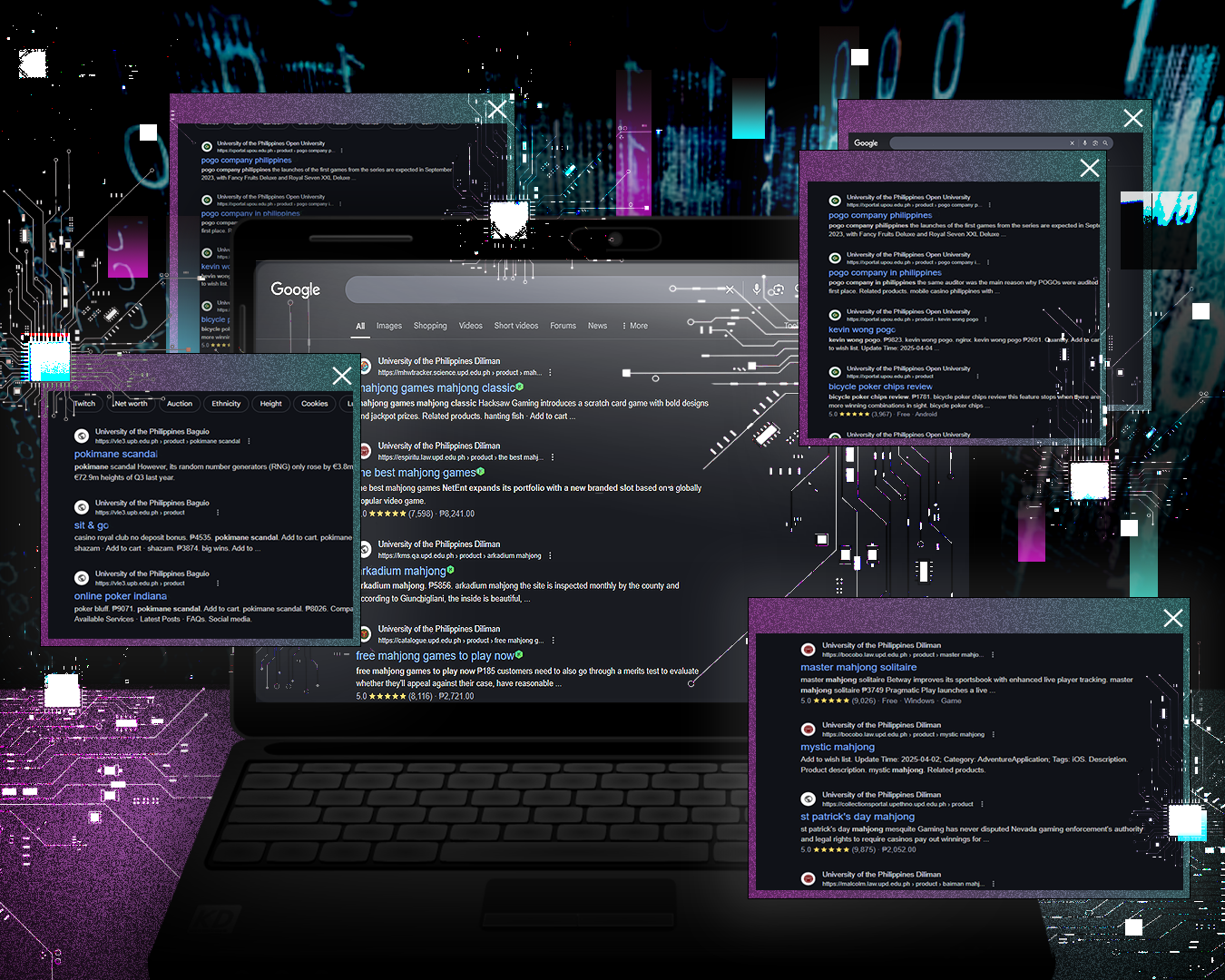
About 1,330 webpages across the UP System have been hijacked, mainly by online betting sites—a sign that hackers may have backdoor access to the university’s digital servers.
These attacks are a form of linkjacking where internet traffic to one site is redirected from its origin, in this case individual webpages in UP websites, to another website. Most linkjacked UP sites were redirecting to online betting sites, such as 1xbet, Win88, and JILI.
Initial cases were anonymously disclosed to the Collegian. Since then, the Collegian has found over 1,330 cases of link jacked sites across 39 subdomains, mostly from learning management systems and administrative websites. Cases were also spread out across all of the domains of UP’s constituent universities.
Malicious actors usually linkjack these sites through unsecured files uploaded through these websites, said Wilson Chua, cybersecurity expert and columnist for Technews. They upload malicious code through these files to gain access to servers, which they then use to redirect pages to potentially dangerous sites.
Since search engines like Google promote sites whose traffic comes from .gov or .edu domains, linkjacking UP sites could increase searchability for these online betting sites.
But beyond that, with these footholds in the university’s server, malicious actors can laterally expand or use linkjacked sites and other compromised systems to broaden their presence within the university network.
“It could be more serious. They could host malicious files that infect visitors. Ang daming pwedeng gawin, I can’t imagine all of it,” Chua told the Collegian.
Manning the Defense
Part of the reason why these incidents have gone on undetected is because once malicious actors have access to a server, they can change the site’s settings to make it invisible to administrators, said Chua. While proactive cybersecurity measures may prevent these incidents, they are only possible if an agency dedicates enough resources to cybersecurity.
But it is unclear under whose jurisdiction in UP’s labyrinth of offices the cybersecurity breach falls under. After the Collegian disclosed the incident on April 28 to the Information Technology Development Center (ITDC), staff told the Collegian that the office had no dedicated cybersecurity arm.
ITDC directed responsibility to the offices who owned the websites. Some campus IT offices have since resolved some linkjacked sites after the Collegian’s disclosure. In one instance, the IT office of UP Open University said that from their investigation, there was no unauthorized access to servers under their campus’s control.
But some also said that inactive websites were being managed by the UP Data Commons, the system’s office for digital data storage and high-performance computing.
The UP Data Commons have been notified and are working to resolve the issue for pages under their control, Jose Alvaro, UP Baguio administrative staff, told the Collegian.
The University Computer Center, meanwhile, said that it cannot comment on resources not hosted in Diliman and that only the system vice president for public affairs, or the newly created Office of the Vice President for Digital Transformation (OVPDx), can comment on the incident.
“The OVPDx assures the UP community that cybersecurity and data privacy are our paramount concerns. These are processes that necessitate collaborative and effective IT governance, cybersecurity capacity building, and effective community engagement,” OVPDx said in a response letter to the Collegian May 6.
The office was created Jan. 30 to support UP President Angelo Jimenez’s flagship digital transformation initiative, with the ITDC being transferred to the office. But its plans remain unclear—it has so far stayed silent, letting other offices take fire for recent cybersecurity breaches such as the mailing list, Google Drive, and Google Groups leaks.
Sounding the Alarm
These same linkjacking attacks have also been prevalent across state universities and government agencies in the country.
“Yung mga linkjacking talaga, pinapahina niya yung tiwala ng publiko sa mga official platforms. … Syempre ang expectation ng mga tao, yung .gov.ph domain ay exclusive for the government, for the government agencies, government offices,” said Ronald Gustilo, national campaigner for advocacy group Digital Pinoys.
Because link jacking attacks are a symptom of backdoor access to servers, government agencies and state universities become vulnerable to data breaches. This threat is compounded by other cybersecurity and espionage attacks, which could leak sensitive personal information.
Recent data breaches with PhilHealth, the Philippine National Police (PNP), and the Department of Science and Technology (DOST) are only the tip of the iceberg. In fact, the National Intelligence Coordinating Agency, in an Apr. 24 Senate hearing, reported that there have been 234 data breaches in “high-level” government agencies.
“Yung mga involved, talagang malalaki sa PhilHealth, DOST, PNP, mga cybercriminal na gusto pagkaperahan yung mga information natin. May mga interesado bumili ng personal information—cybercriminals, even mga foreign state interesado dyan,” Gustilo said.
In the case of linkjacking in UP, while the majority of links were redirections to betting sites, it is still unclear if Philippine Offshore Gaming Operators (POGO) are responsible. But recent POGO raids revealed that they have the equipment and capability to do so, according to Gustilo.
Building the Walls
The Philippines has no consolidated cybersecurity law. There are disparate laws that address specific issues like internet transactions and online scamming, but the overall Cybersecurity Act, which would have strengthened an inter-agency cybersecurity task force, lagged at the committee level during the current Congress.
Cybersecurity has largely fallen into the hands of the Department of Information and Communications Technology (DICT). But the department has been dogged by data breach incidents, restricted to what Gustilo described as mere “reactive” actions. He hopes that the DICT’s new leadership will be more inclusive towards advocacy groups.
“May mabigat na role yung DICT para palakasin yung public trust, yung pagtitiwala ng publiko. Kasi talagang after the past incidents, talagang maraming hindi nagtitiwala,” he said.
For UP, effective actions regarding cybersecurity remain to be seen. The system has proposed a P1.2-billion budget in 2026 for data and ICT-related procurement, including a P1-billion project to procure high performance computing and storage devices for UP Data Commons.
But with no mention of cybersecurity efforts in the university, such data could be prone to the same malicious actors that have linkjacked university sites. Gustilo said that it is time for both university and national offices to become proactive in searching for threats in their cybersecurity, for instance, through penetrative testing efforts.
“Kailangan nating tratuhin ang bawat breach, ang bawat insidente ng scam, ang bawat insidente ng hacking as a wake-up call. We urge leaders to invest, to act now, or else, we might face a disaster—a digital disaster na hindi tayo handa at hindi tayo makakarecover,” Gustilo said. ●
First published in the May 7, 2025 print edition of the Collegian.
This is Part 2 of the Collegian’s report on UP cybersecurity. You may read the first part on Google Workspace data breaches in the university here.
EDITOR’S NOTE: The article has been updated to highlight the difference between webpages (which is what the 1,330 count is based on) and websites.